How to use command prompt to hack wifi ferprice
Add this topic to your repo. To associate your repository with the hacking-tools topic, visit your repo's landing page and select "manage topics." GitHub is where people build software. More than 100 million people use GitHub to discover, fork, and contribute to over 420 million projects.
5+ Best CMD command used in hacking Popular Command used in Command Prompt
Let's start with a simple attack. If we have the username and password that we expect a system to have, we can use Hydra to test it. Here is the syntax: $ hydra -l
how to hack a website with cmd (anonymous is back) YouTube
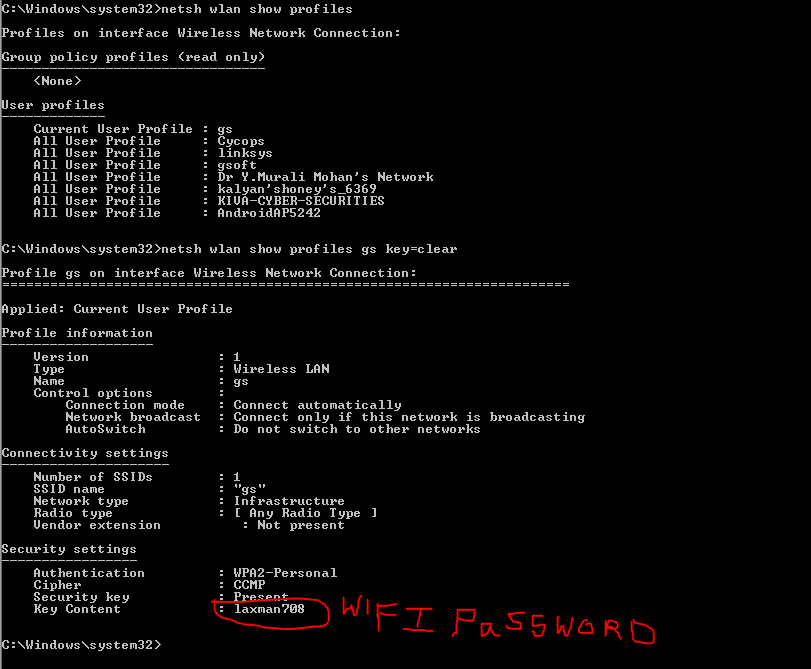
1. Encrypting the files using CMD : It is the most useful command to encrypt or decrypt the folders or files without using any third-party apps. Search for CMD in windows search (windows key + S). And open CMD. Just type " Cipher /E" then hit on enter this will encrypt all the files in the current directory. To decrypt type "Cipher /D".

Cmd hacking tutorial nimfacricket
1. Find a vulnerable site where you can post content. A message board is a good example. Remember, if the site is not vulnerable to a cross-site scripting attack, then this will not work. 2. Go to create a post. You will need to type some special code into the "post" which will capture the data of all who click on it.

Top CMD commands used in Hacking Beginners YouTube
The following tools are additional ways to truly elevate your hacking game. wttr.in — There's only one right way to check the weather. 2. Star Wars — Cool people like Star Wars. Hackers watch it in the terminal. telnet towel.blinkenlights.nl Pro Tip: Watch star wars in another tmux pane while working. No one will question you. 3.

Best CMD Commands Used By Hackers In Hacking Coding Area YouTube
Add this topic to your repo. To associate your repository with the web-hacking topic, visit your repo's landing page and select "manage topics." GitHub is where people build software. More than 100 million people use GitHub to discover, fork, and contribute to over 420 million projects.

CMD HACKS Best Way To Look Like a Hacker YouTube
ping www.google.com -t. Note: Replace www.google.com with the website on which you want to perform the DDoS attack. c. You will see the IP address of the selected website in the result. Note: IP address will look like: xxx.xxx.xxx.xxx. 3. After getting the IP address, type the below command in the command prompt.
Best Command Prompt Hacks and Tricks Techonloop
Web Hacking. 12. JSParser: A python 2.7 script using Tornado and JSBeautifier to parse relative URLs from JavaScript files. This is especially useful for discovering AJAX requests when performing security research or bug bounty hunting. 13. Knockpy: Knockpy is a python tool designed to enumerate subdomains on a target domain through a word list.
7 Best CMD Commands Used In Hacking, The Ultimate Guide YouTube
Times Touch - If you want to use command prompt on Windows 10 more efficiently you should know some CMD tricks. Well we bring you 10 hidden Command Prompt.
Top 3 Best CMD Command Used In Hacking How To Tips » Tech Hacks, PC Tricks, Hacking Tutorials
The cmstp command installs or uninstalls a Connection Manager service profile. The cmstp command is available in Windows 11, Windows 10, Windows 8, Windows 7, Windows Vista, and Windows XP. Color. The color command is used to change the colors of the text and background within the Command Prompt window.

Two Hacking Pranks Using Windows Command Prompt (cmd) Ι FEATURED YouTube
Click the Start Menu, type "cmd" (no quotes), and the menu will show a Command Prompt; right-click that entry and select Run as administrator. That'll open the black box full of text with the.

How do hackers get into computers through websites snosecurity
F2: Pastes the last executed command (up to the entered character) F3: Pastes the last executed command. F4: Deletes current prompt text up to the entered character. F5: Pastes recently executed commands (does not cycle) F6: Pastes ^Z to the prompt. F7: Displays a selectable list of previously executed commands.

CMD commands for Hackers Hack Networks using Windows YouTube
How can I clear access granted or access denied? Hit ESCAPE to clear "Access Denied/Granted". Start HackerTyping. Troll your friends and coworkers with Hacker Typer's Hacker Prank Simulator. We make it look like you're coding like a real hacker. Just start typing, we'll do the rest ;)
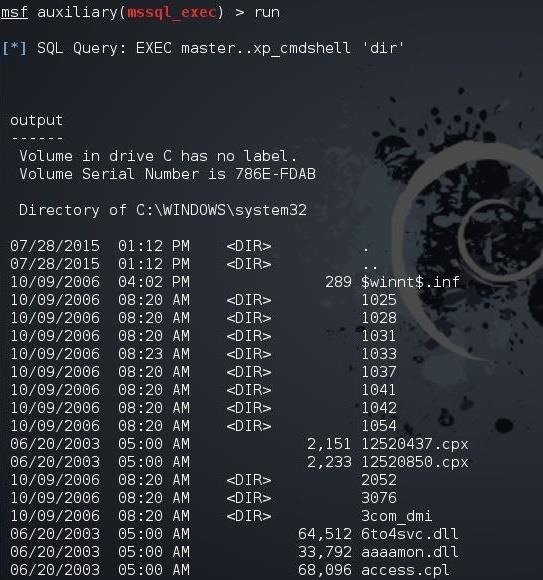
TUTORIAL HACKING CARA HACK WEBSITE CMD
Introduction. Disclosures of breaches often include mention of a "web shell" to further attacker ends. As one example, the Clop ransomware group (also known as 'Lace Tempest,' TA505, and FIN11) has used web shells as part of their attack chains in both the Kiteworks Accellion FTA breach 1 of 2020 and the plethora of breaches related to Progress Software's MOVEit software 2 in 2023.
Best CMD Commands Used In Hacking Ultimate Guide to Windows
1. Customize Your Look. You may know this one already, as it can be a great tool to play around with for accessibility purposes. Command Prompt can be fully customized, from background and text color, font, opacity, and more. Right-click on the Command Prompt icon in the upper left-hand corner. Of the screen.
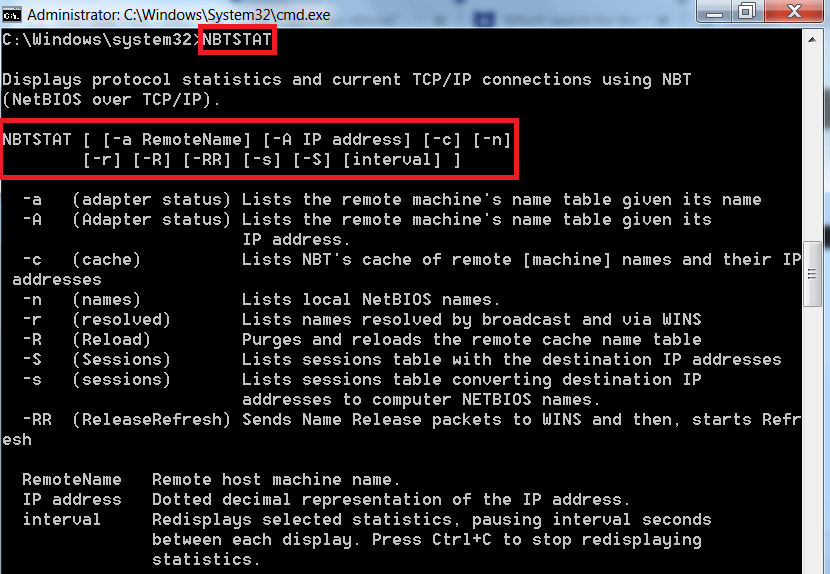
Cmd hacking codes list
Method 1: Windows key + R -> type cmd -> press Enter. Method 2: Windows key -> type cmd or command prompt -> left-click on the CMD icon. Now that Command Prompt is up and running, it's time to have some fun. We're going to start with a couple of basic commands and then move on to the more advanced stuff.